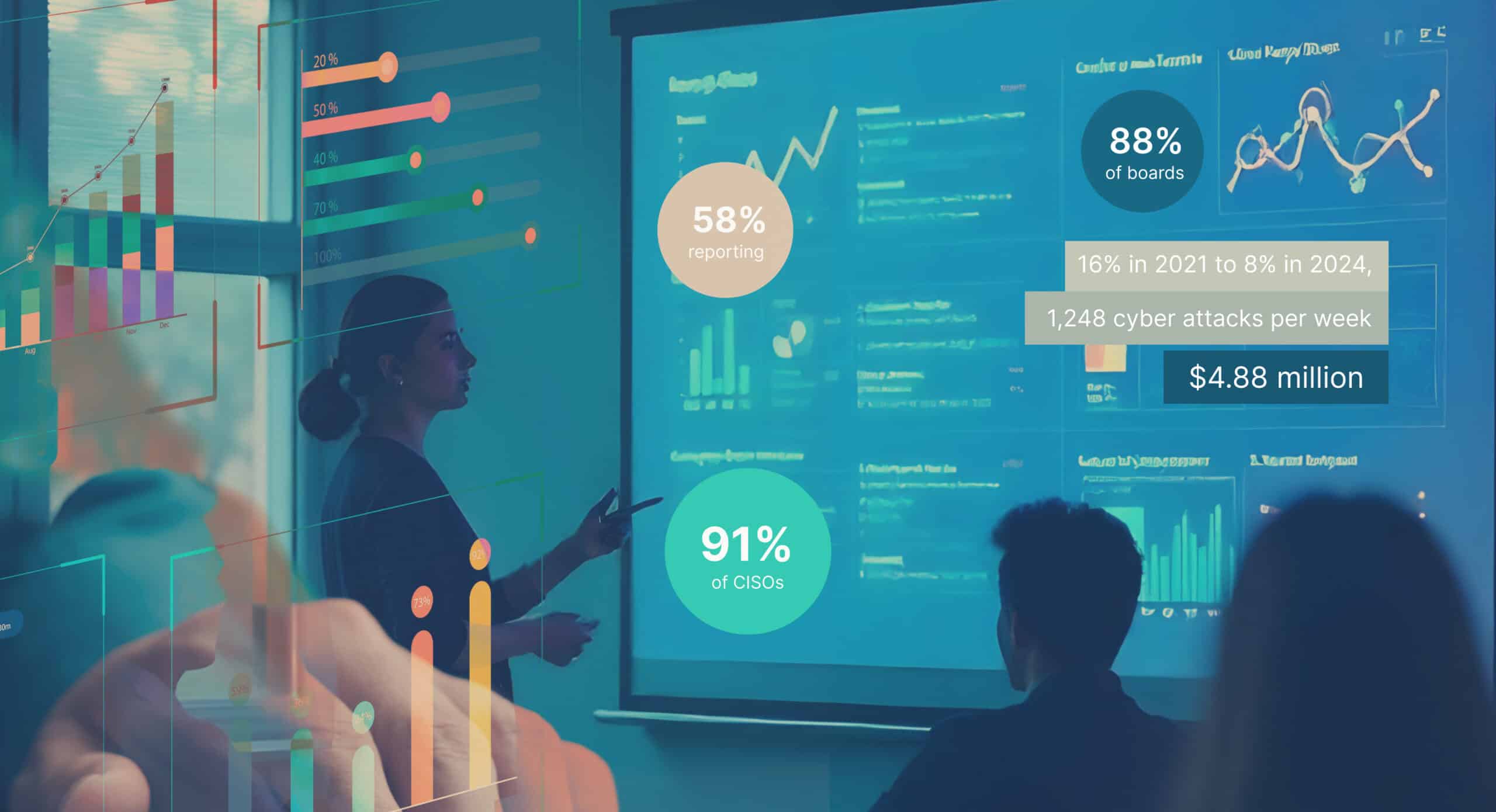
In Q1 2023, organizations faced an average of 1,248 cyber attacks per week. With the average cost of a data breach reaching $4.88 million and dwell times still averaging 204 days, Chief Information Security Officers (CISOs) are under unprecedented pressure to demonstrate effective cyber risk management. CISOs are reporting directly to the board these days and must do so in a way that board members can grasp and easily understand. They are also under immense pressure to guarantee an acceptable level of risk while ensuring that their work doesn’t impede the product development teams that fall under the CTO, which drive innovation and grow top-line revenue for the company. While these seem like unrelated challenges, they have a convergence point. What is it? Security data analytics – not merely as a tool or approach but as the basis for a fundamental transformation in how security leadership operates, communicates, and proves its value.
The Data-Native CISO: A Necessary Shift
The modern threat landscape and contemporary demands on security necessitate a new approach to security leadership. Cybersecurity is now a vital function within businesses, and cyber threats, an essential component of a company’s risk profile. The numbers reflect this reality – a Gartner survey reports that 88% of boards view cybersecurity as a business risk rather than merely a technical issue. While cybersecurity’s importance has been elevated, resulting in the presence of the CISO in the boardroom, 91% of CISOs say that they aren’t communicating security risks to their boards very effectively. This is in part due to the highly technical nature of cybersecurity and the fact that there hasn’t been a simple way for CISOs to gather and analyze real-time security data and transpose it into language that non-technical board members can easily understand.
This transformation from technical expert to data-driven business leader isn’t just about being prepared for board meetings – it’s about creating a competitive advantage by making intelligent investments that help minimize risk. The drop in security budget growth from 16% in 2021 to 8% in 2024, combined with the shortage of qualified and experienced cybersecurity talent adds pressure on CISOs to be simultaneously more effective and efficient. These trends are forcing CISOs to get more discerning with their investments and derive more value from them. Given the fact that companies that use data-driven automations saved an average of over $2.2M per breach and saw their time to identify and contain a breach lowered by nearly 100 days on average, it makes sense that CISOs should focus on leveraging data as a force multiplier.
A data-native approach to security has numerous benefits, ranging from improving board-level reporting and interactions, to better risk management and resource allocation.
Transforming Reporting and Interactions with the Board
Effective leadership and board communication is a critical challenge for CISOs, with 58% reporting difficulty translating technical metrics into business terms that can be easily digested. Part of the challenge is the highly manual nature of developing board-level metrics. Many CISOs still use spreadsheets to develop and track security metrics, but the data and corresponding insights are often siloed, which makes it difficult for CISOs to confidently prioritize among the different security risks their companies face, and correspondingly, allocate resources to burn down that risk. They rely on experience or gut-feel, which require that the board trusts the CISO’s judgment – a luxury many CISOs do not have.
Another challenge CISOs face is that the spreadsheet-driven approach makes it almost impossible to incorporate business data into their calculations, which renders the insights that they provide severely lacking in overall business context. In the boardroom, there’s little time or appetite to dive into cybersecurity minutiae, and CISOs must find ways to translate what they know about their environment into a clear, concise, prioritized list of risk items that are accompanied by their corresponding business impact and associated expense.
The current expectation of CISOs is that they enter the board conversations as a contributor of data into the company’s decision-making process, and not merely serve as a harbinger of doom. The rest of the C-suite is already armed with synthesized data and scorecards to inform decisions that affect the entire company, and CISOs must transform their practices to match their peers.
Improving Risk Management and Resource Allocation
One of the primary expectations of the CISO is that the security team adequately protects the business’s assets. However, not all business assets are the same. Some Lines of Business (LOB) may be more valuable than others, and hence, represent a larger risk. Logically, these LOBs should be prioritized when it comes to allocating resources towards risk burndown. However, in reality, it is difficult to parse risk in this manner.
Historically, the only way to tease the insights that enabled more accurate risk prioritization was to build your own data pipelines. This is an initiative that requires a significant amount of investment and effort. However, organizations that do so gain immense clarity about their risks. That knowledge, combined with cyber risk quantification data, enables organizations to calculate the annual loss expectancy (ALE) associated with the risks, which makes prioritization and resource allocation much easier to determine. As a simple example, if the risk level for two separate LOBs are the same, but one of them contributes significantly more to the company’s revenue and bottom line (resulting in a higher ALE), the choice is obvious – address that LOB’s risk first. This is a significant benefit of being data-native – greater certainty about which risks to prioritize, and where to allocate resources.
Improving the Security and Engineering Dynamic
While both the office of the CTO and the office of the CISO are technically on the same team, in practice, the relationship can be a little fractured and, in some organizations, absolutely broken. The challenge is that the primary mission of both organizations results in Key Performance Indicators (KPIs) that are fundamentally opposed to each other.
The CISO’s goal is to get risk down to an acceptable level and ensure that anything that elevates risk is reduced or eliminated. Most of those risks are found in the digital products and services the company develops, which are produced by the CTO’s organization. The CTO’s goal is to innovate, build new products, and ship as quickly as possible to meet product and revenue goals.
When security teams discover security vulnerabilities that developers have to fix, the product development teams are slowed down, and they push back, demanding that the security team accurately prioritize the vulnerabilities they have to fix so that they don’t waste time on less important ones. The challenge is that today, there’s no good way of prioritizing that risk in a way that ensures that the vulnerabilities that could have the greatest impact on the organization are the ones that are tackled first, as security has to perform manual analysis to determine which of the numerous individual security alerts to focus their efforts on. The result is that development teams and security teams end up on opposite sides of the argument about what and how much to work on vulnerability fixes.
A data-native CISO would be armed with a data-informed understanding of the organization’s security risks within her company’s business context and a clear view of which part of the organization owns the risk. That would allow her to partner with her engineering counterpart to identify which engineering team should address the risk and allocate resources effectively to tackle the vulnerabilities that have the most potential impact on their business. This objective, shared view will go a long way towards ensuring harmony between the security and engineering organizations.
What Do CISOs Need to Become Data-Native?
In order for CISOs to adopt a data-native approach, a few things must be present. The first is a commitment from the entire organization to embrace this approach. Going from spreadsheets and intuition to making decisions based on data is a fundamental shift that requires organizations to rethink some of their processes and tools.
When data is at the core of all decision-making processes, it becomes necessary to make investments in data capture, storage, processing and analysis. Security data is unique because it can change state, and conventional data management engines that manage log data struggle with dynamic security data such as vuln data, cloud misconfigs, and EDR alerts. A solution that supports the ideals of a Cybersecurity Mesh Architecture (CSMA) would provide immense value from the data that security tools collect. This means that organizations must also invest either in building their own security data pipelines or in a tool that can manage this dynamic data.
Whether homegrown or a commercially available solution, a data management engine like this would enable other security tools to interoperate and magnify their effectiveness. It would also provide security leaders with the ability to perform consolidated policy management, accurate and contextual risk management, simplified board reporting, and automate tedious manual processes such as compliance evidence collection.
Conclusion
Given the speed at which the threat landscape evolves and businesses move, organizations must embrace security data analytics as a core component of their security efforts. Traditional approaches to risk management, board-reporting, and vulnerability fix prioritization are fast becoming archaic. We’ve not even addressed the implications of Artificial Intelligence (AI), as both a contributor to the expanding attack surface for organizations, or as a lever that can be pulled to further increase the effectiveness of security teams. Unsurprisingly, data lies at its heart.
The successful security leaders of the future will be those who can harness the power of data to drive better decisions, communicate more effectively, and deliver measurable value to their organizations, while those who neglect this shift will be left behind.
Want to learn more about how data-native CISOs are getting the type of insights that help simplify their risk management and board-level reporting without having to invest in lengthy, complex, and expensive data pipeline building projects? Schedule a conversation with us to learn more.
About Dassana
Dassana is a leading provider of security intelligence solutions. Dassana revolutionizes the process of security data aggregation and normalization, empowering organizations to extract vital insights to expedite time-to-remediation, enhance the productivity of security teams, and ultimately bolster the effectiveness of security controls. Learn more about Dassana on LinkedIn or at www.dassana.io.