✕
Risk-based Vulnerability Management & Attack Surface Management
Dassana Remediate
It’s about time. Find the needle in the haystack.
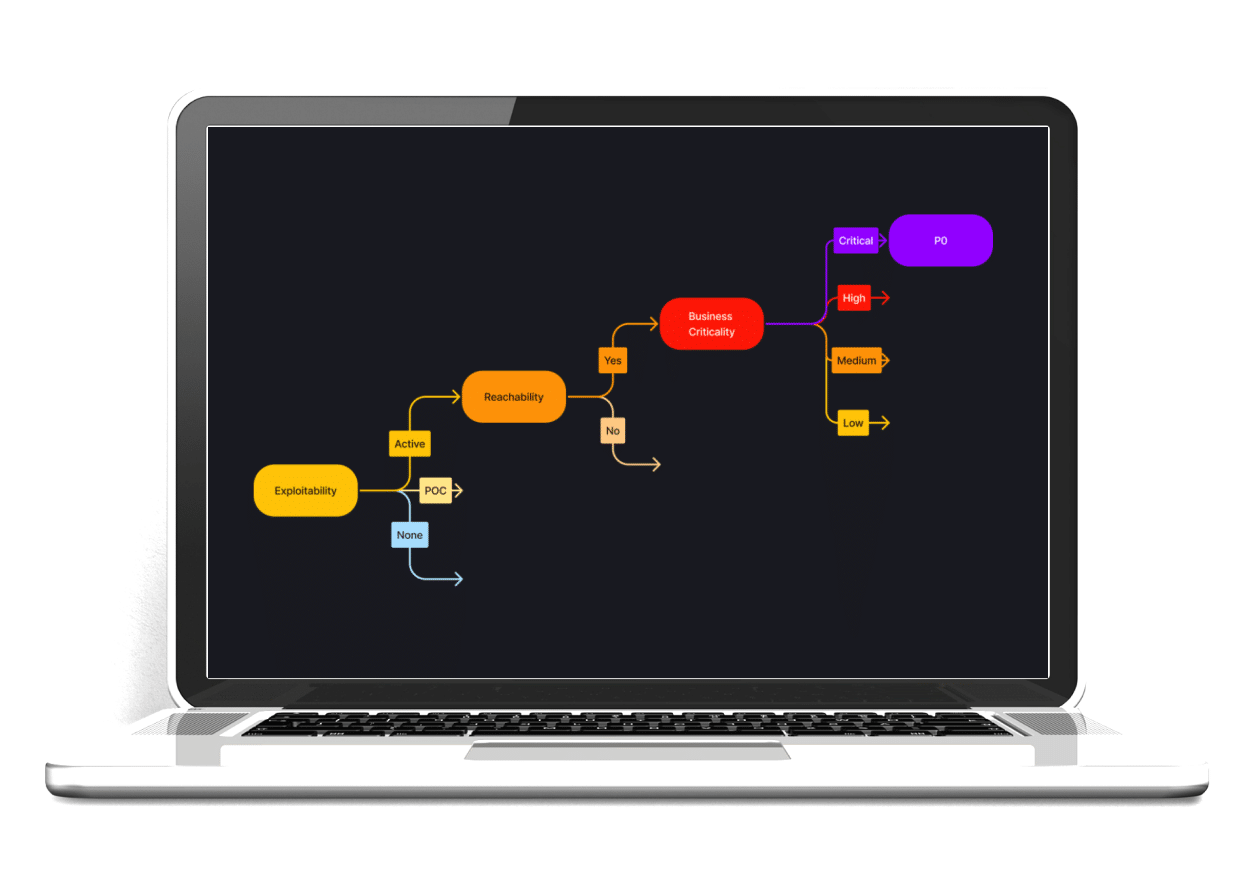
Welcome to risk-based vulnerability and attack surface management. By marrying data from security tools, external threat intelligence, and most importantly, business context, Dassana provides true explainability behind what needs to be addressed, by when, and why now.
Manage your vulnerability overload.
Having trouble grasping and addressing the vulnerabilities crucial to your business using a combination of spreadsheets and hope? We firmly believe there’s a better approach. Discover how you can mitigate the risks stemming from inefficient vulnerability prioritization and remediation methods. Fix fewer issues and enhance security significantly.