Investigative journalism has “follow the money”; in security, it’s “follow the data.” Both lead to the truth.
Security is not just about building walls and guarding gates; it’s inherently a data problem. Viewing security through the lens of data simplifies an otherwise complex field.
The Complexity in Simplicity
Let’s consider a hypothetical, paper company, Dunder Mifflin. The company has employees like Michael Scott and Dwight Schrute who manage both physical and digital assets. The security team ensures that every asset logs relevant data (stateless record of events). They also purchase various security controls to protect their users and assets, which generate findings.

The Layer of Acronyms
The challenge lies in understanding these four basic components—users, assets, events, and findings—especially when viewed through the complex lens of security.

The Challenges of Tool Overload
Investing in security tools is the easy part. Measuring their efficacy and ROI is where it gets tricky.
Each new tool exacerbates two significant productivity gaps: misaligned priorities and visibility issues.

Vendor-Locked Reality: Navigating the Maze of Tool-Specific Priorities
Every security tool in the marketplace generates its own set of findings, often lacking the contextual relevance needed for effective action. To make matters more complex, each tool features its own unique system of prioritization. This presents a dilemma: when disparate tools offer conflicting to-do lists, which tasks should be prioritized?
Relying solely on a single tool for security insights is equally problematic. Such a narrow focus effectively ‘pigeonholes’ the perspective, limiting overall visibility. To counter this, many enterprises resort to building DIY data pipelines for a more comprehensive view. However, these solutions are not without their challenges. The initial setup can cost an organization as much as $175k in the first year, with an additional $95k in the subsequent year for expanded reporting needs.
Furthermore, these custom pipelines are not infallible. They are prone to malfunctions and downtime, leading to stale or inaccurate datasets. At such junctures, the reliability of an organization’s security measures comes into question, raising concerns about operating under a false sense of security.

The Data-Centric Approach
Last week, we discussed breaking these silos by using Security ETL—either with a connector or without. By centralizing all this data, we can start to comprehend the organization as a whole.
The Incentive Game: Understanding Scanners and Aggregators in Cybersecurity
When it comes to scanning, more is often perceived as better. Scanners are inherently designed to sweep as much of an environment as possible, generating a plethora of signals in the process. This ‘more is better’ approach is a direct result of the incentives driving these tools. The crowded marketplace has pushed scanners to scan extensively, creating a deluge of data that can overwhelm customers. Consequently, many scanners have taken a step back, disabling the majority of their policies by default to mitigate customer fatigue.
This raises an important question: Shouldn’t customers have the freedom to activate all available and relevant policies without overwhelming their systems?
Enter the role of aggregators. Unlike scanners, the primary incentive for aggregators is to sift through the noise and hone in on the critical signals. This creates a contrasting dynamic, where one tool is incentivized to generate data while the other is motivated to distill it.
Making Sense of Data
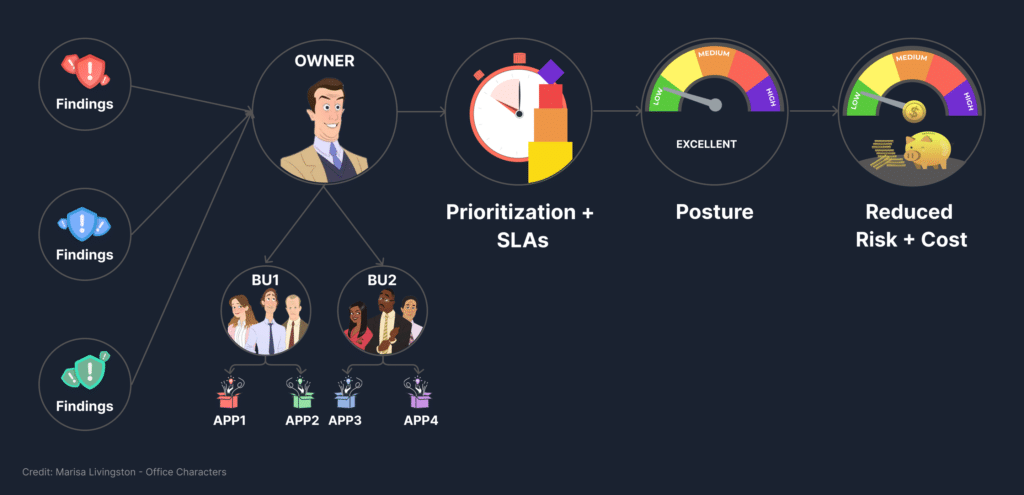
Understanding the organization means going beyond the org chart. It involves leveraging tags, naming conventions, and other attributes to identify asset ownership and business context.

Global Prioritization
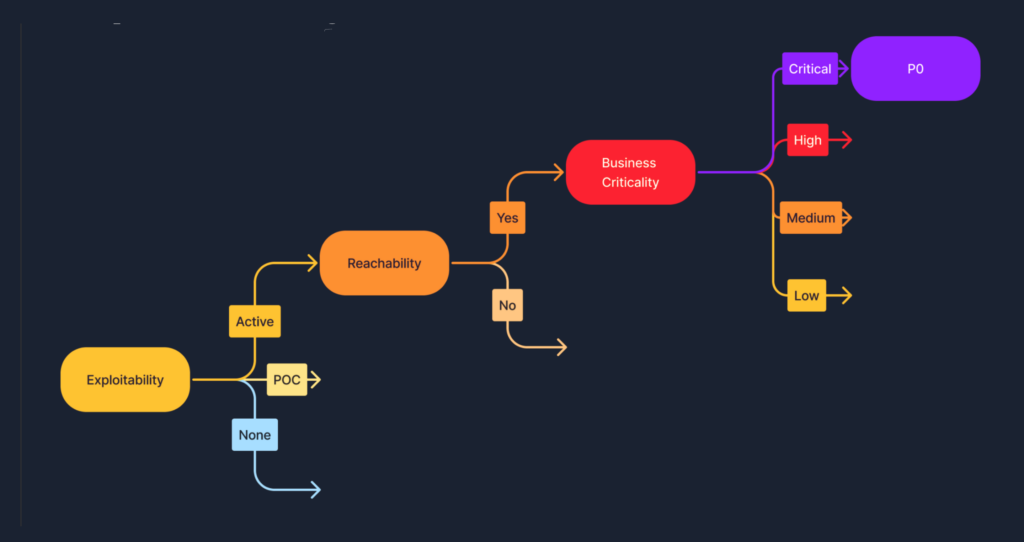
By centralizing all data and incorporating external threat intelligence, the stage is set for effective global task prioritization. Here, the concept of ‘explainability’ takes center stage. It combines Business Context, Exploitability, and Reachability to pinpoint the most pressing issues that demand immediate attention.
The Last Mile: Automation
Identifying immediate needs is only half the battle. The final step involves automation, channeling tasks through appropriate platforms like JIRA or Slack notifications.

The Security Lifecycle
By focusing on data, we can traverse the entire security lifecycle with ease: Ingestion, Normalization, Attribution, Prioritization, and Orchestration.

The Benefits of a Data-Centric Approach
A data-centric approach answers pivotal questions such as identifying blind spots and assessing significant risks. In the event of an incident like the infamous log4j vulnerability, a data-centric strategy offers both visibility and an automated action plan. This proactive preparation ensures that the relevant stakeholders and the BoD stay informed, rather than reaching out in a crisis with no plan in place.
In a landscape rife with acronyms and ever-evolving threats, maintaining a data-centric perspective simplifies security. By focusing on data, centralizing it, and automating responses, organizations can navigate a labyrinth of confusing signals to establish a streamlined, effective security posture.