In past discussions, we explored the transformative potential of security ETL, emphasizing data ingestion, normalization, and visualization. We then ventured into the intricacies of automated orchestration. With that foundation, we now turn to a pressing question: Why should we prioritize understanding behavior in the world of security metrics?
The Essence of Behavior
The dynamic world of cybersecurity presents a myriad of metrics. But do we genuinely grasp what these figures represent? Our driving force is the relentless pursuit of effectiveness. This journey is steered by a shift from mere isolated risk metrics to a comprehensive behavior-centric viewpoint.
Drawing Parallels: Credit Scores and Cybersecurity
Imagine the sting of your credit score dropping after a valid, albeit significant, purchase. Feels unfair, doesn’t it? Drawing a parallel, it seems illogical for security scores to plummet upon the discovery of a new 0-day vulnerability. Such a metric evaluates extraneous events instead of an entity’s actual behavior.
Introducing the Security Behavior Score

Taking cues from systems like the FICO score, which evaluates creditworthiness based on behavior, the Security Behavior Score transcends mere risk quantification. It assesses response effectiveness, examining how promptly organizations address vulnerabilities and their adherence to global SLAs. This approach fosters a forward-thinking, ever-improving security culture.
Beyond Vendor Severity: Crafting Contextual SLAs
Merely anchoring SLAs to vendor-provided vulnerability severities is myopic. It’s vital to imbue SLAs with context, considering factors like environment, criticality, reachability, and mitigating factors. Such granularity dismisses the notion of “alert fatigue.” By undertaking global prioritization and contextualization, organizations can discern genuine priorities. These, when tracked against their SLAs, offer an authentic gauge of behavior.
Global Prioritization: A Strategic Compass

With a clear grasp of organizational priorities, security teams can pinpoint the vulnerabilities or threats that demand urgent attention. This isn’t just about reactive measures; it emphasizes informed, strategic action.
Risk Through a CISO’s Lens
All risks aren’t alike, nor do all warrant elimination. It’s about discerning which risks are tolerable and which aren’t. Such insight empowers CISOs to judiciously allocate resources, focusing on significant risks while accepting those intrinsic to business functions. It’s a journey of informed decision-making over chasing an elusive zero-risk scenario.
Delving into Key Metrics
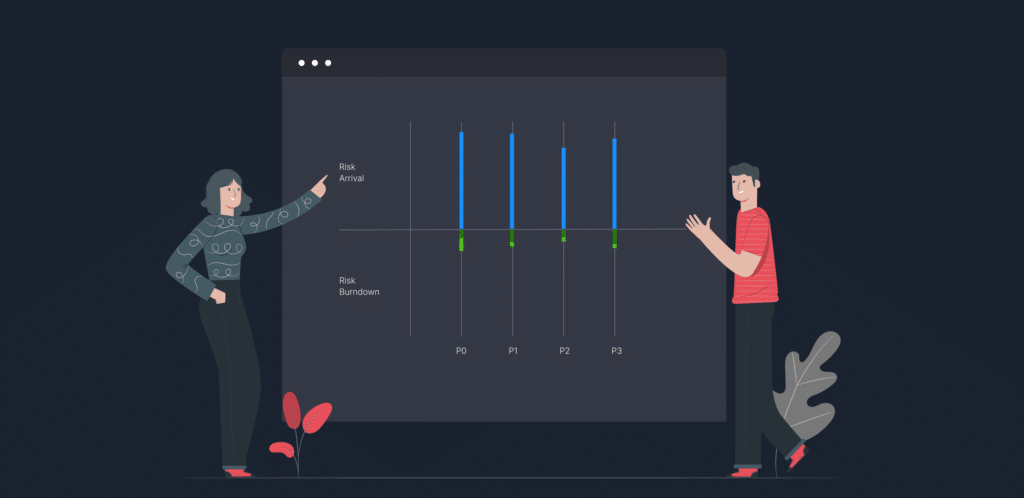
Risk Arrival and Survival: How frequently do new risks emerge, and how long do they persist?
Risk Burndown and Escape Rates: What’s the pace of risk mitigation, and what manages to elude?
Interarrival Time: What’s the interval between consecutive critical risk detections? Are teams in perpetual reactive mode, or do they have respites to address other risks?
Richard Seiersen’s Metrics Manifesto eloquently elucidates these metrics, illuminating the broader risk landscape and any residual risks post-mitigation. These insights ensure that mitigation strategies truly bolster security, surpassing mere compliance checkboxes.
The essence of future cybersecurity transcends mere defense. It hinges on perpetual betterment, effectiveness, and crafting security strategies harmonized with business goals. By championing behavior and genuine productivity boosts, we’re not just fortifying our defenses; we’re laying a robust foundation for businesses in this digital epoch. Understanding, embracing, and astutely managing risk will illuminate our path, steering us to a more robust, agile business horizon.